According to SonicWALL researchers, ransomware attacks more than doubled from 2021 to 2022. As a result of this increase, many organizations found that their cyber insurance providers now required they implement air-gapped backups to protect their critical data. In this post we will look at air-gapped backups by answering the question…What are they and how are they implemented?
What are they?
Air-gapped backups are backups that are kept perpetually isolated from the network that produced them.
How are they implemented?
When looking at how to implement air-gapped backups, the expression that “there’s more than one way to skin a cat” applies. Rather than enumerate all the ways to do so - some of which are complex, others costly - we will outline one that is both simple and cost effective while arguably being equal-to or better than the alternatives. We will start with a sample backup architecture that is not air-gapped…
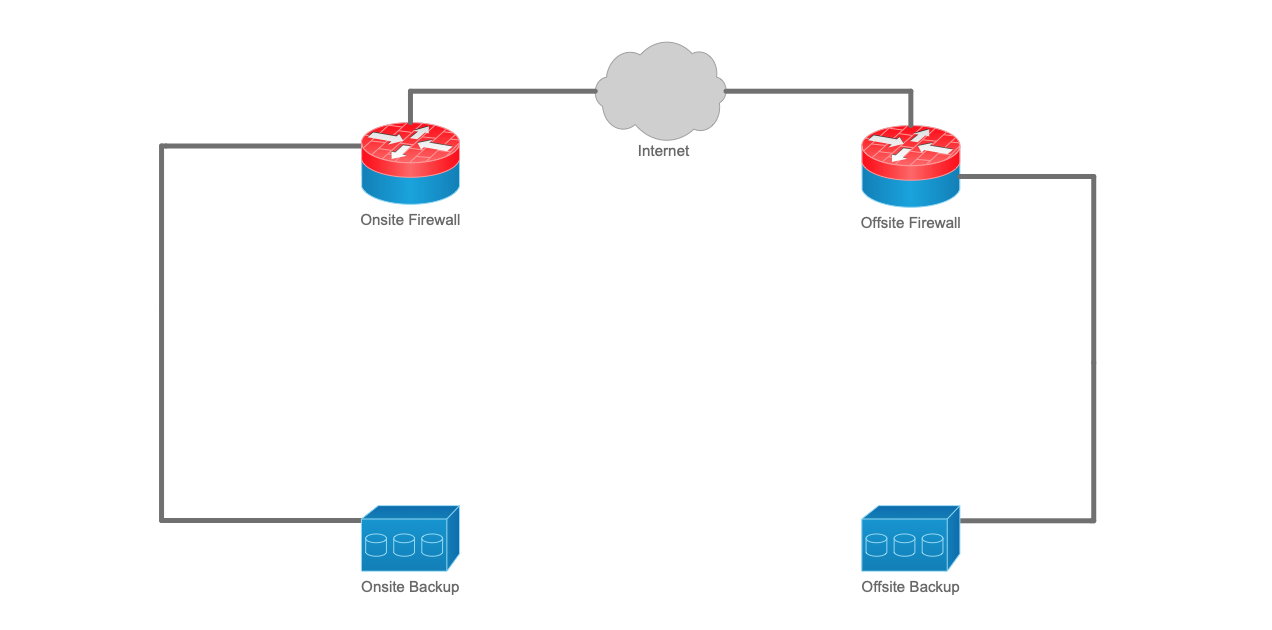
Figure 1. Non Air-Gapped Backup Architecture
As can be seen in the diagram above, this backup architecture consists of an onsite and offsite location. Each location is protected by a firewall which also provides VPN connectivity between them. In such an architecture, the onsite backup can be copied to the offsite location thereby achieving best practice of keeping “1” copy offsite (i.e. a 3-2-1 backup strategy).
By using straightforward network design and intelligent power distribution units, the backup architecture outlined above can be converted to one that is air-gapped…
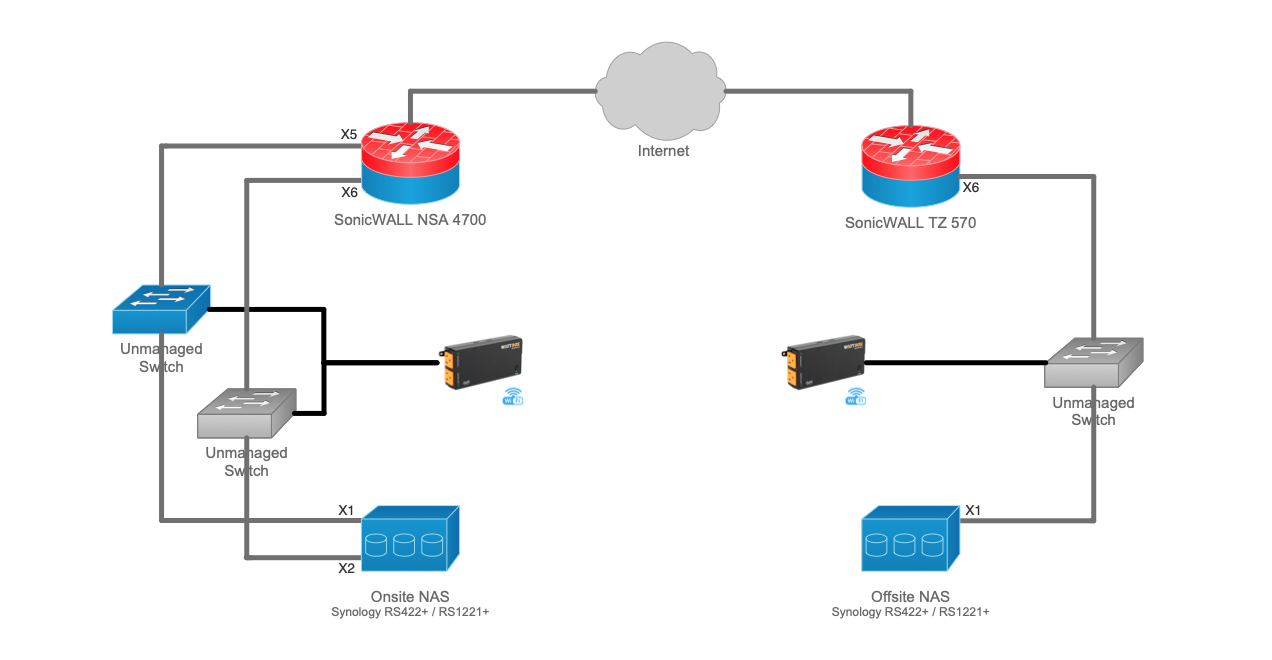
Figure 2. Air-Gapped Backup Architecture
Make & models are noted above for reference purposes only and can be changed or substituted as needed
The changes made to do so follow:
- A network segment (X6<>X2) was added to the onsite firewall to isolate connectivity between the backup devices from the primary onsite LAN (X5<>X1)
- Unmanaged (e.g. 5-port) switches were inserted on each link between the firewall and their respective backup devices
- Intelligent power distribution units were added to provide power to the unmanaged switches
With these changes in place the following state machine can be implemented to keep the backup devices perpetually isolated from the primary onsite LAN:
- Default state. In this state normal backup activity takes place on the primary LAN.
- Onsite: Power on to unmanaged switch (US) connecting X5<>X1. Power off to US connecting X6<>X2.
- Offsite: Power off to US connecting X6<>X1.
- Backup state. This is a scheduled state in which the backup devices are isolated from the primary onsite LAN and data can be copied from the onsite to the offsite backup device.
- Onsite: Power off to US connecting X5<>X1. Power on to US connecting X6<>X2.
- Offsite: Power on to US connecting X6<>X1.
- Return to Default state.
That’s it! A design that relies on scheduled power distribution to enforce network isolation. Simple while being equal-to or better than any alternative.
Next Steps
If you have questions or would like like to discuss a requirement you’re facing today, feel free to contact us by calling 919-244-4375 or sending an email to sales@vigilnetworks.com.